*We recommend Cyber Essentials to all our clients to make sure they have a layer of protection against email phishing 365, which we can provide, please contact us for more information.
Phishing with Fake Microsoft 365 Login Pages
This is one of the most common and dangerous phishing techniques used to compromise Microsoft 365 accounts — including Outlook, Teams, OneDrive, and SharePoint.
How Email Phishing 365 Works
- User receives a phishing email or link
- It might say:“You have a secure document waiting”“Reset your Office 365 password”“Unusual login detected”
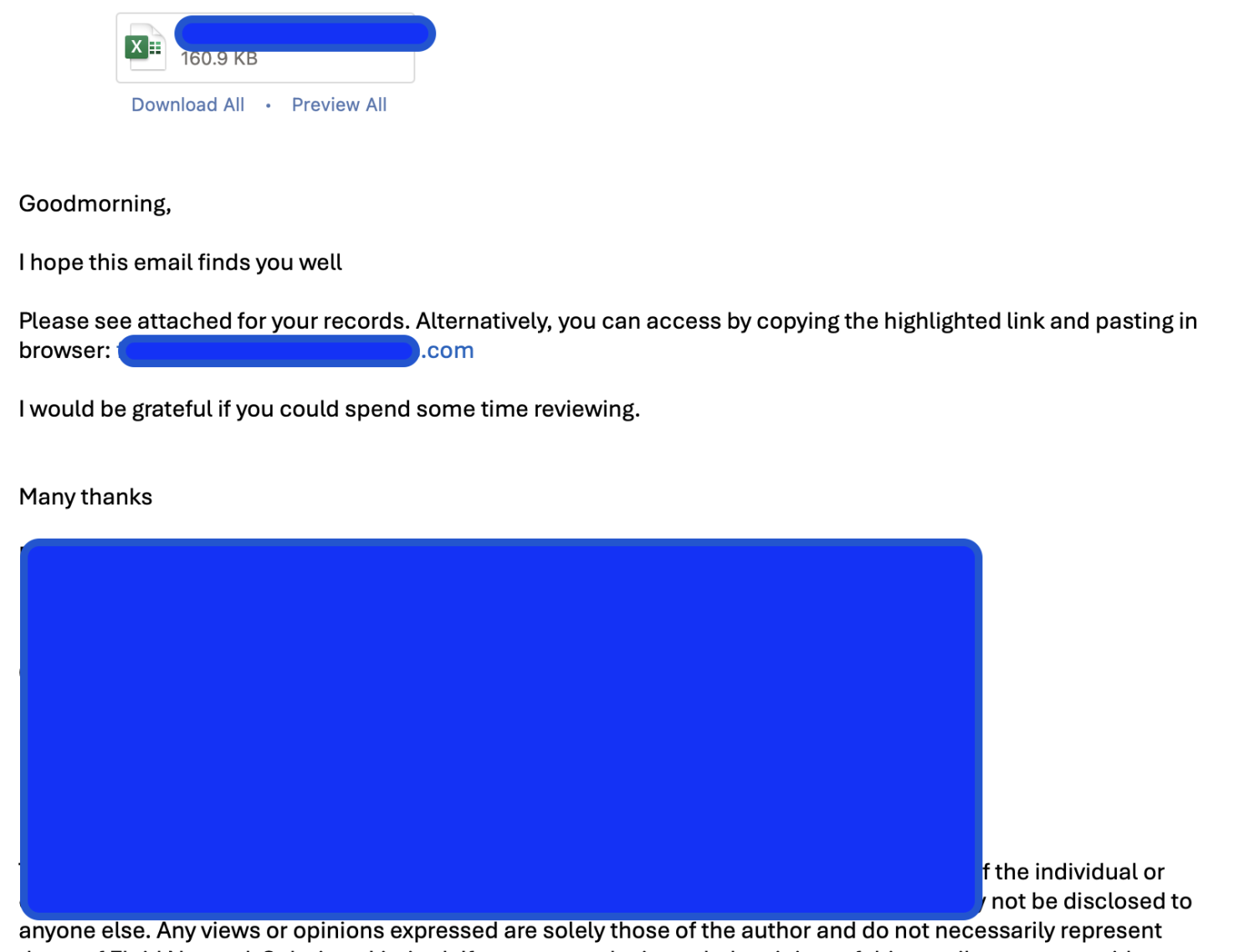
- It might say:“You have a secure document waiting”“Reset your Office 365 password”“Unusual login detected”
- User clicks the link
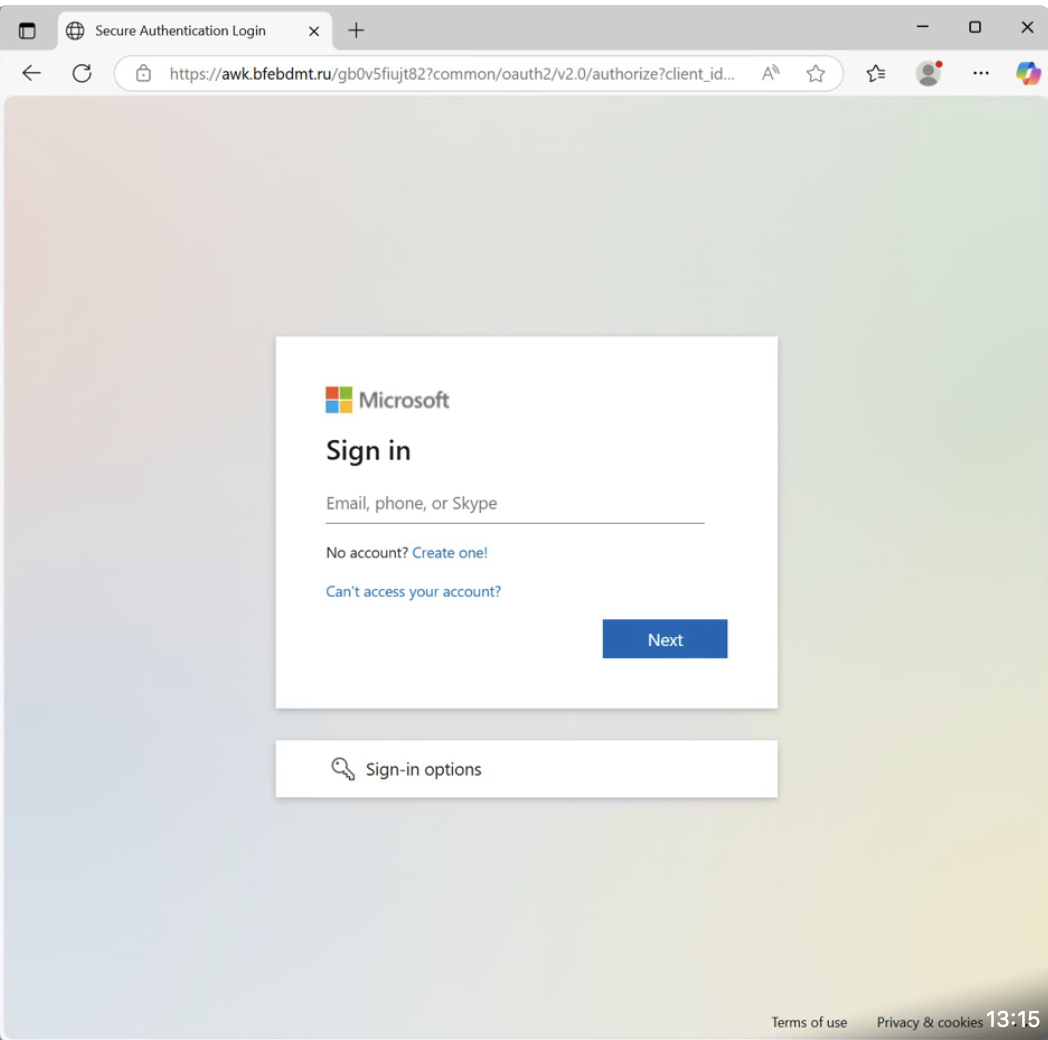
- It goes to a fake login page that looks exactly like the real Microsoft 365 sign-in (e.g., login.microsoftonline.com).
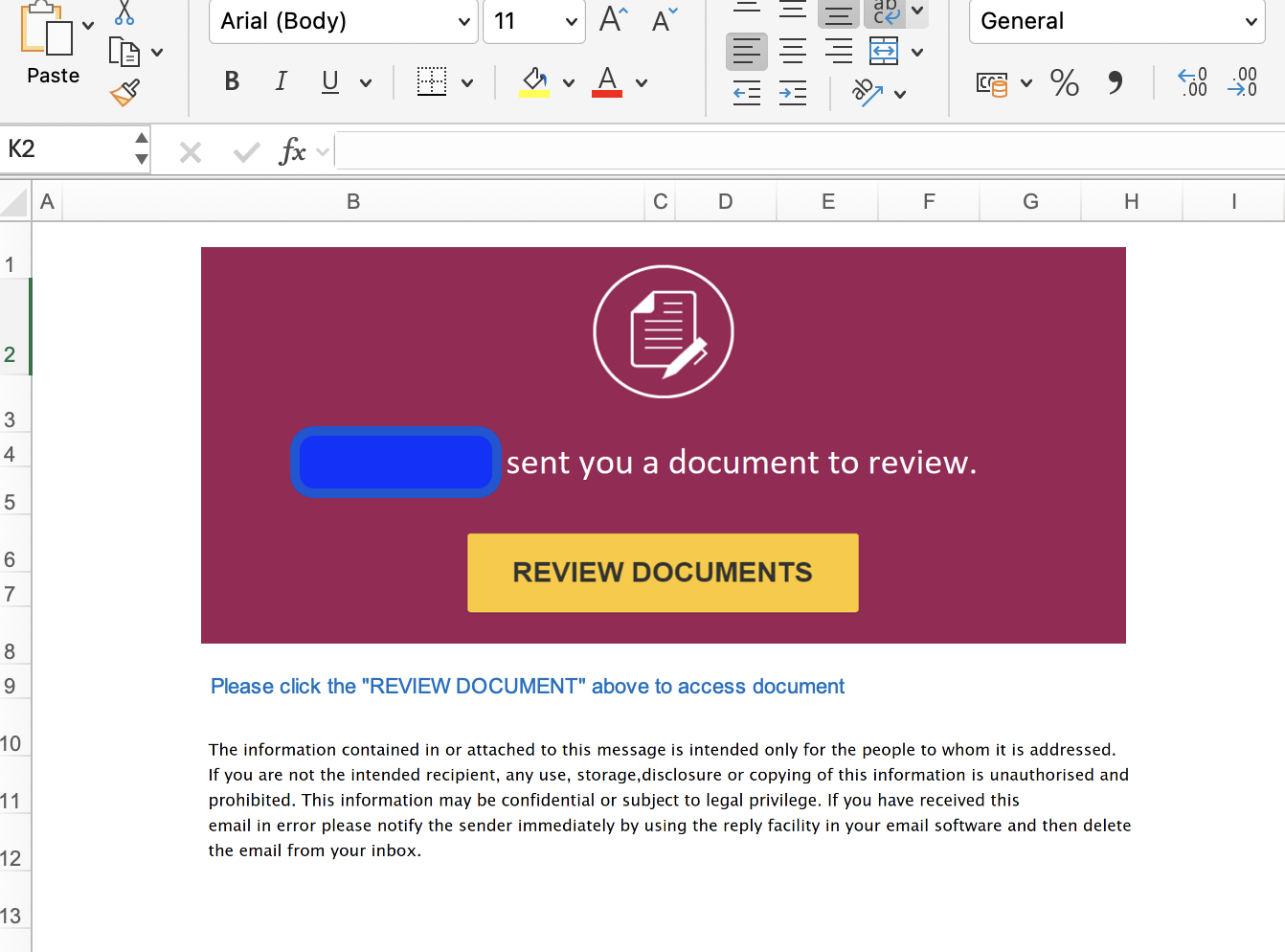
- It goes to a fake login page that looks exactly like the real Microsoft 365 sign-in (e.g., login.microsoftonline.com).
- User enters their credentials
- The attacker captures the username & password in real time.
- Some fake pages can also capture MFA codes or session tokens via reverse proxy techniques.
- Attacker logs in to the real M365 service using:
- Captured credentials
- Stolen session tokens (to bypass MFA)
- Or OAuth tokens granted to malicious apps
Tools Used in These Attacks
- Evilginx2, Modlishka, Muraena → advanced phishing toolkits that act as a reverse proxy to Microsoft’s real login
- Fake static HTML pages → simpler kits that mimic the login UI without proxying
- Cloud-based hosting
Fake Page:
- Looks exactly like the real M365 login
- May even load real images/scripts from Microsoft
When the user enters:
- Credentials are sent to attacker’s server
- The attacker logs in immediately
- If MFA is used, attacker may:
- Prompt the victim to enter the code (real-time relay)
- Or steal session cookies (if using reverse proxy)
What Attackers Do After
- Business Email Compromise (BEC)
- Set up mail forwarding rules (e.g., forward invoices or wire transfer approvals)
- Gain access to Teams, SharePoint, OneDrive
- Send phishing emails to other users in the org (lateral movement)
Educate Staff
Train users to:
- Hover over links
- Check domain spelling
- Recognize “urgent” language in emails
- Use Microsoft Authenticator app notifications carefully
Spot a Fake M365 Login Page
| Clue | Real Microsoft 365 | Phishing Page |
|---|---|---|
| URL | https://login.microsoftonline.com/ | https://microsoft365-verify-login.com/ |
| Certificate | Issued by Microsoft | Unknown CA or misspelled |
| Page Load | Fast, secure | May be slow or glitchy |
| MFA Handling | App or text prompt | Asks for code in browser again |
Contact Shropshire Computers to find out how we can help you protect your business.